Faced with year-on-year rising attack figures, law enforcement have struggled to adapt to the immense task of preventing ransomware and cyber extortion. By tracking and analysing attacker reported victim data, we seek to explore the significance of Lockbit’s recent takedown in the context of prior disruption efforts.
TL;DR
- On the 20th February 2024, Lockbit ransomware were disrupted by a bilateral law enforcement operation including the UK’s NCA, the FBI and several international partners, reportedly via a critical PHP vulnerability.
- According to JUMPSEC data, Lockbit accounts for an average of 26.2% of total victims globally (from 2021-present) making them the most prolific ransomware entity, having targeted over 2,000 victims and receiving an estimated ~$120M (DoJ).
- Unlike previous action to takedown REvil prior to the Ukraine invasion in 2022, the physical arrest of the group’s Russian-based actors is no longer possible in the current geopolitical landscape.
- However, authorities arrested two LockBit actors in Poland and Ukraine, issuing 8 warrants, seizing infrastructure, freezing 200 crypto accounts and developing open-source decryption tools to aid victims.
- This follows the arrest of two Lockbit affiliated threat actors in late 2022 and 2023.
- Authorities also publicly trolled the largest ransomware group to date and damaged their reputation, breeding doubt into their network and potentially affecting Lockbit’s affiliate actor recruitment power.
Disruption in context: How do Lockbit compare?
With many speculating on what will happen next, here’s a timeline of the historical data from previous instances where ransomware groups of a comparable size to Lockbit were shut down or disbanded, running from 2021 to March 2024..
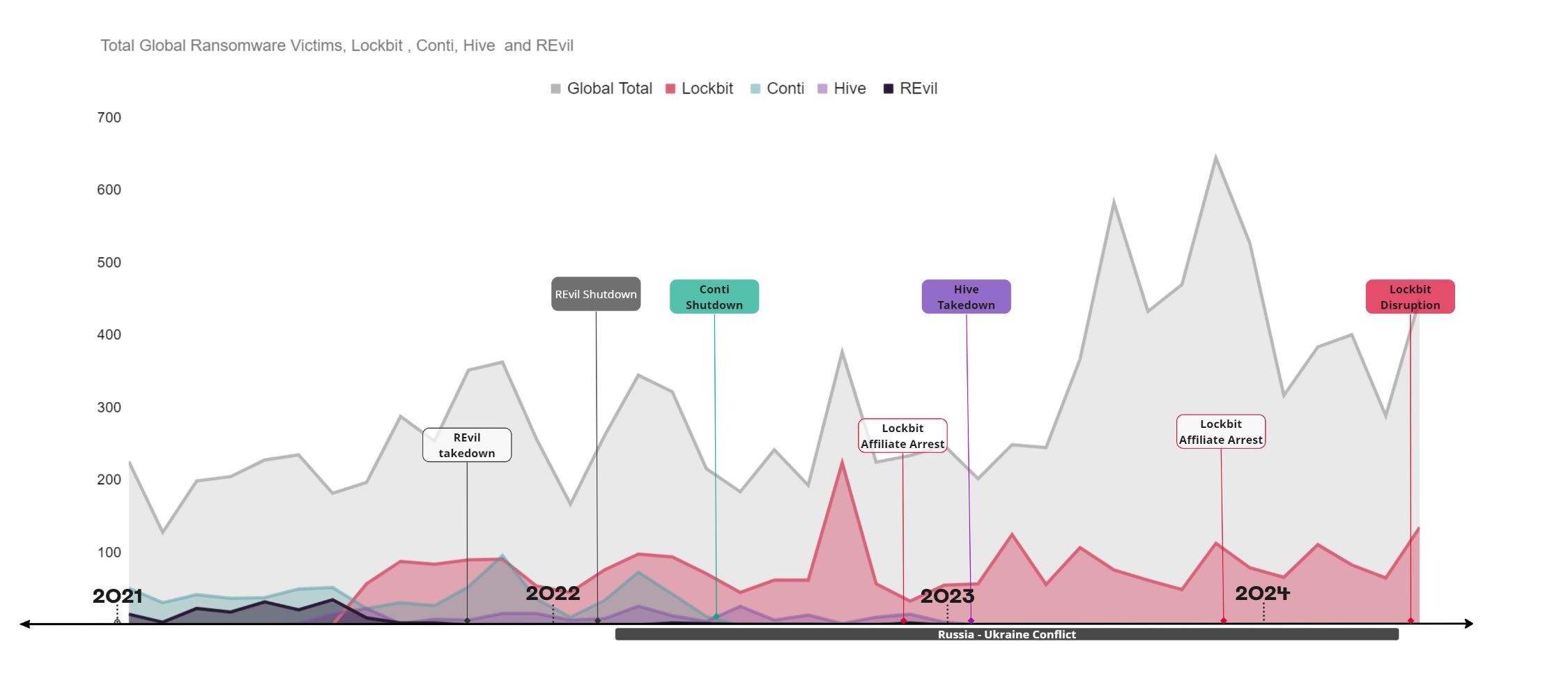
Above: Lockbit’s proportionate share of global victims has been significant at ~26.2%. The total number of ransomware victims globally (grey), along with the monthly victims of the major ransomware groups (Lockbit, Conti, Hive and REvil) that have now been disrupted or disbanded, 2021-2024.
If ongoing attempts by Lockbit to re-start operations are ineffective or their presence naturally diminishes, emerging or less prolific competitors could capitalise by recruiting additional technical resources and affiliates still keen to profit from ransomware.
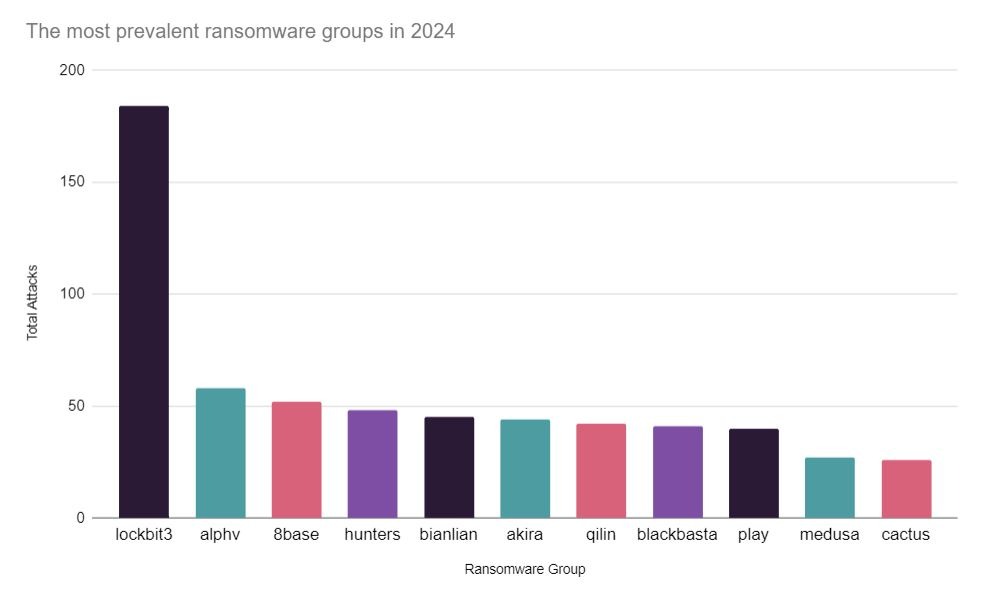
Above: The most prevalent threat actors so far in 2024. As we have seen previously, as one group dissolves or diminishes, others may rise (i.e connected groups Conti. Karakurt, Royal, or REvil and BlackCat).
Each major ransomware takedown has provided a unique insight into threat group disruption. Below we breakdown the REvil, Conti, Hive and Lockbit disruptions.
REvil/Sodinokibi (October 2021)
One of the most notorious ransomware groups, REvil, had their servers compromised and were forced offline in a bilateral law enforcement operation in October 2021 before being aggressively arrested by authorities in a suspicious show trial-esque Russian police raid in January 2022 prior to the invasion of Ukraine. Whatever its true significance, the potential for Russian threat actors to face physical consequences is now next to impossible.
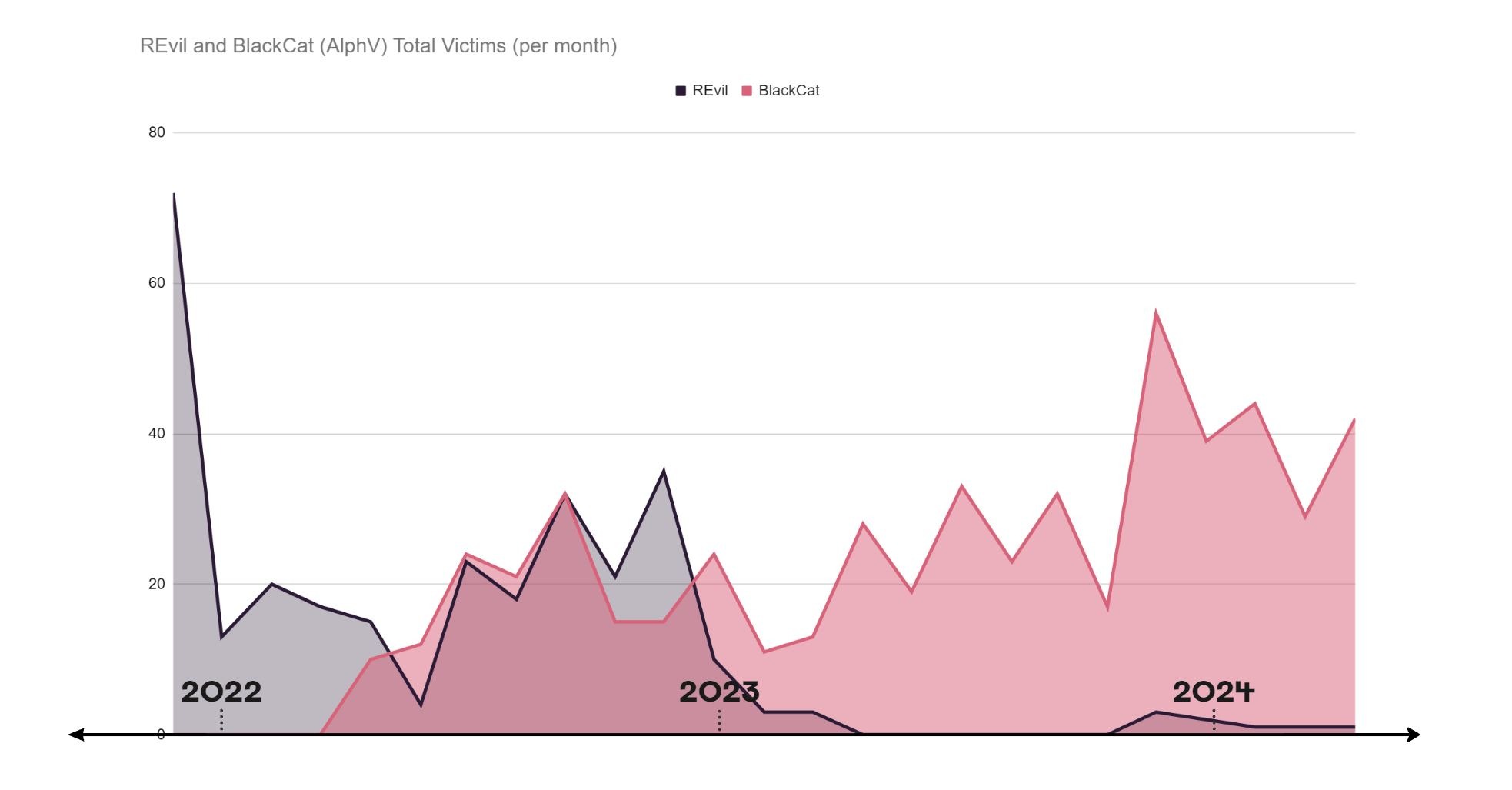
Despite disappearing as ‘REvil’, potentially connected groups such as BlackCat continued to grow. So too have Karakurt, Royal and Akira after Conti’s dissolution (connections based on aligned TTPs and reputable CTI).
Conti (May 2022)
Conti were one of the few groups to have a comparable impact as Lockbit, with an average of 17% of global total victims during its lifespan. Conti increasingly targeted high-risk targets (i.e the Costa Rican Government) and the group’s dissolution was ultimately due to increasing law enforcement pressure and in-fighting between Russian and Ukrainian members surrounding national allegiances in late February 2022.
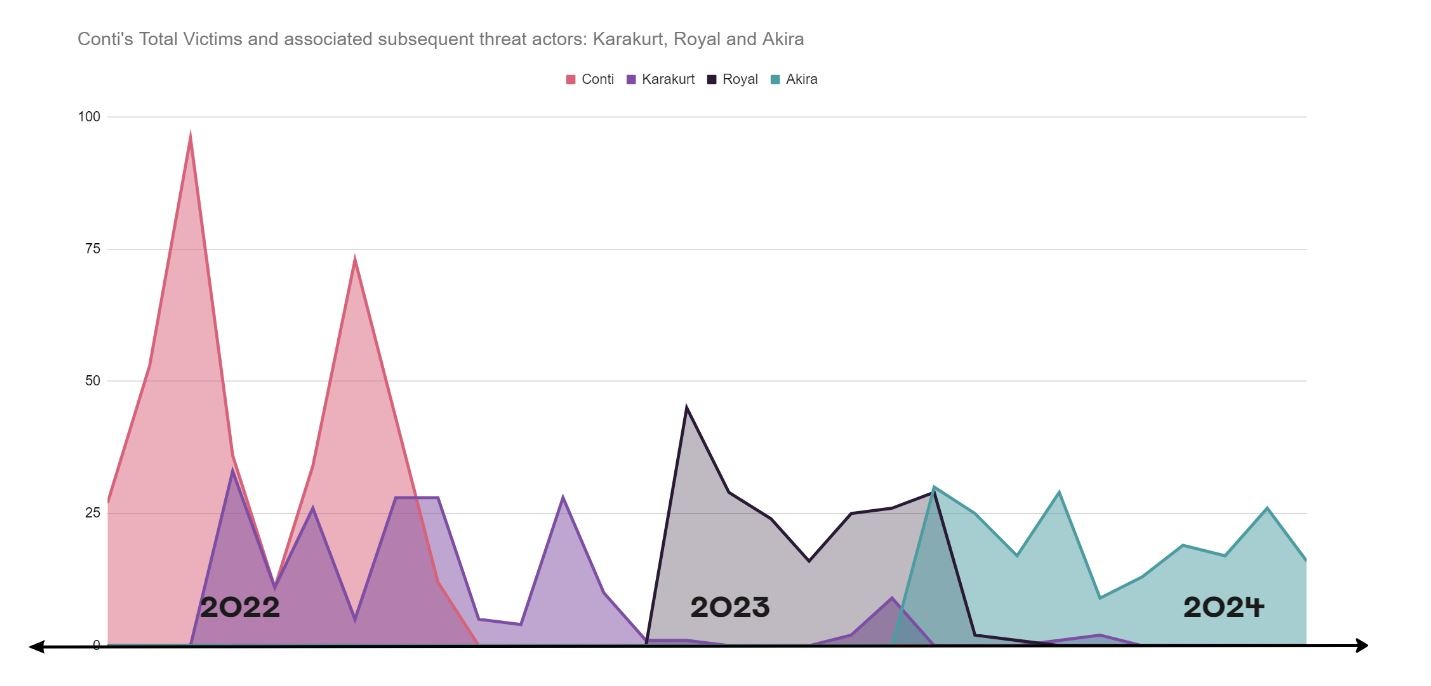
Like REvil, following Conti’s dissolution, Karakurt, Royal and Akira emerged as more prolific entities. There is evidence to suggest that these groups were connected with Conti members based on aligned TTPs and available CTI.
Hive (January 2023)
The takedown of Hive ransomware encompassed a bilateral law enforcement operation saw several US and European crime agencies collaborating to infiltrate Hive’s infrastructure, distributing decryption keys, and thwarting a reported $130million in ransom payments.
Requiring the concerted effort of several national crime agencies over a six-month period, the takedown demonstrated the scale of the challenge in tackling ransomware groups directly, as the relatively small ransomware group was a drop in the ocean of total attack figures. That said, official statements that announced the operation as a ‘model for future success’ have aged well.
Conclusion
Ultimately, while the cynics may correctly point out that previous takedowns have not seriously impacted the long-term rise of total ransomware victims, the disruption caused by the NCA, FBI and other law enforcement agencies should be acknowledged as a major win. Beyond the display of technical prowess and the limiting of Lockbit’s capabilities, by posting the NCA and FBI logos on Lockbit’s site and setting a timer threatening to reveal the admin’s identify, authorities are playing the threat actors at their own game.
Hopefully, the fact that authorities are confident enough to ironically troll the most significant ransomware group to date is a signal that international law enforcement have developed the technical capacity and cohesion to seriously disrupt more advanced and sustained ransomware threats. Equally, one can only hope that Lockbit, who continue to operate, are unable to seek significant retaliation for the authorities’ experimental tactics.
While Lockbit are still posting victims at a similarly high volume, time will tell how effective recent disruptions efforts have been.


