Why we took this approach
There is a clear incentive for organisations who are the victim of data theft and extortion to downplay the severity of a breach, as we explored in a recent article. Organisations have been known to claim the data stolen is outdated, particularly where data theft alone has occurred (without ransomware deployment) – making the attack significantly less visible, and therefore easier to brush under the carpet.
While this approach goes some way to bridge the gap between official and unreported statistics, gaps still exist. One of the primary limitations is that the available data is only based on what ransomware groups are reporting. Therefore, there is a potential gap where victims settle the issue before it hits the public eye (and therefore the breach is never reported, in official channels or otherwise).
While we do consider attempts to track further data points, such as the crypto payments made to the wallets of ransomware actors (i.e Chainanalysis) in our analysis, we acknowledge that there are simply too many wallets to track, too many operators, and too many currencies to build a complete picture in this manner. However, this method of analysis nonetheless presents a useful ballpark estimation.
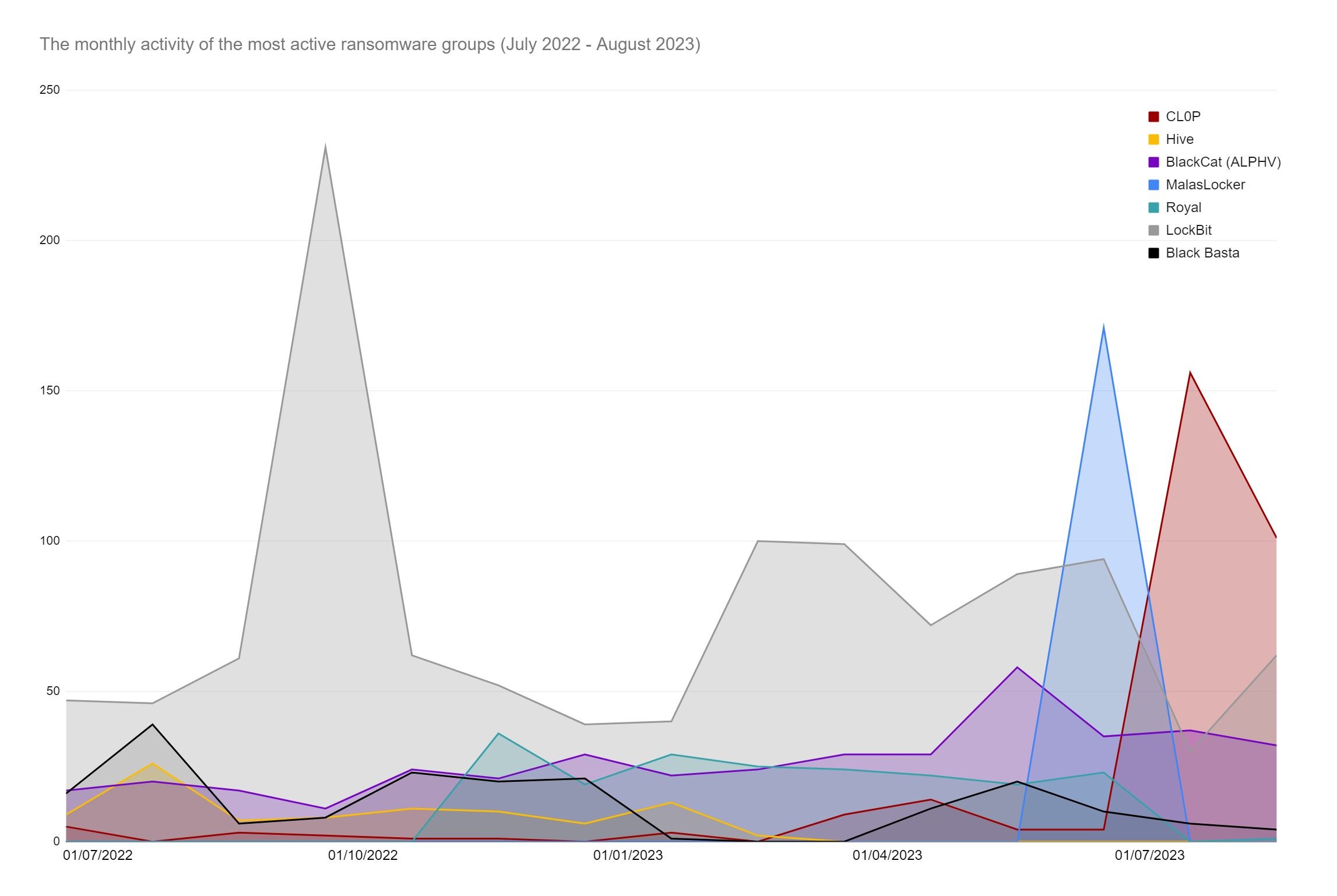
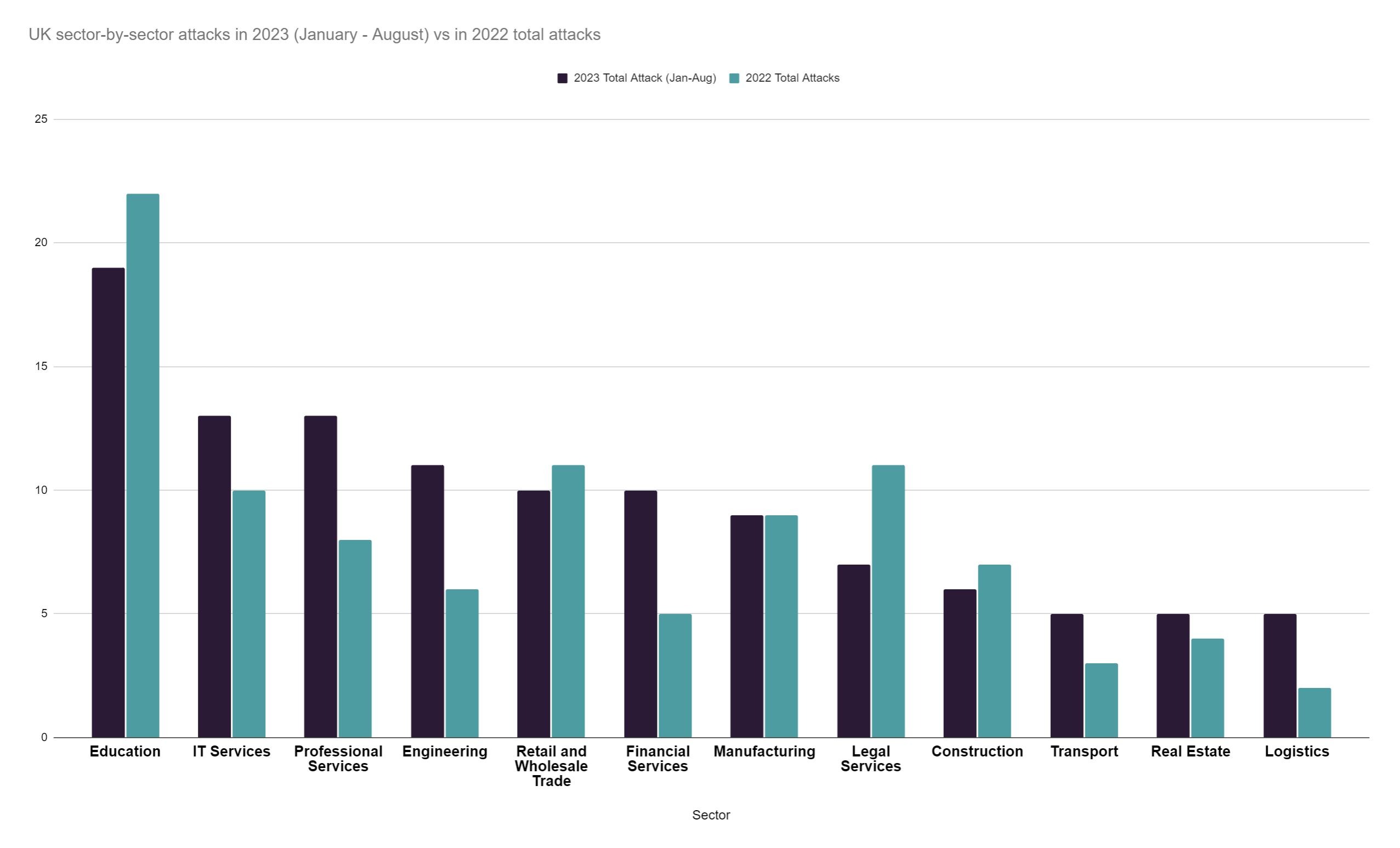
Further, ransomware attacks are not necessarily perpetrated by a single organisation. Initial Access Brokers (IABs) provide a specialised service, gaining access to an organisation’s network and selling this access to the highest bidding ransomware group. Therefore, while particular ransomware groups may appear to prefer to target particular sectors or company sizes, or to have more success in a certain area, IABs may be equally as influential in dictating the trend of which organisations are targeted.
Despite these limitations, we believe a great deal of insight can be gathered from the data (lest perfect be the enemy of progress). We are continually looking to ways to improve the reach and accuracy of our data set by drawing on different information sources, and our analysis will evolve over time as a result.