After reviewing the NCSC Annual Review for 2022, we discuss our 5 key takeaways and give our thoughts on the topic.
Read it here: https://www.ncsc.gov.uk/files/NCSC-Annual-Review-2022.pdf
1. The Impact of the Russia-Ukraine War
The review has a notable focus on the escalating cyber threat posed by Russia. It has been both interesting and frightening to observe the role of cyber alongside traditional “kinetic” military capabilities, with notable attacks on ViaSat and the deployment of the WhisperGate wiper malware against Ukrainian Government targets.
The escalating use of hybrid techniques is something that we should take very seriously when considering the threat to UK infrastructure. Last month, The Centre for Strategic & International Studies published an insightful overview of Russia’s hybrid warfare strategies– explaining “Gray Zone” aggression tactics (including cyber capabilities) – stating that the NordStream sabotage is a wake-up call on the vulnerability of critical infrastructure.
There are early signs of such aggression targeting the UK in the recent damage to the Shetland subsea cables. Although purely speculative at this stage (with the issue just as likely caused by fishing trawlers), a clear trend is emerging. German police are also investigating an act of sabotage on the country’s rail infrastructure in October. While this is yet unconfirmed to have Russian involvement, it prompted NATO to re-state that “hybrid and cyber-attacks can trigger Article 5”, and therefore provoke a response.
In 2023, organisations forming part of the UK’s Critical National Infrastructure (CNI) should consider the potential for hybrid attacks combining cyber and kinetic methods designed to disrupt or destroy key public services. In most cases, cyber remains the optimal vehicle for state-sponsored aggression, with the least chance of discovery, complex attribution, and minimal risk to the attacker. Organisations that are likely targets for Russian aggression should ensure that such scenarios are considered when modelling the risks to the business in 2023, and implement mitigations and business continuity plans accordingly.
Helpful links below:
- Centre for Strategic & International Studies: https://www.csis.org/analysis/five-steps-nato-should-take-after-nord-stream-pipeline-attack
- Sabotage of German Rail Infrastructure: https://www.france24.com/en/live-news/20221009-germany-probes-rail-sabotage-amid-russia-tensions
- JUMPSEC’s Ransomware Report: https://www.jumpsec.com/uk-ransomware-trends-2022/
2. Ransomware’s Continued Growth
The report makes a number of interesting observations that we echoed in our own Ransomware Trends Report.
Over the last year, businesses and organisations in the UK reported hundreds of cyber incidents to the NCSC, 63 of which were significant enough to require a national level response. Of those, the NCSC co-ordinated the national response to 18 ransomware attacks including the attacks on a supplier to NHS 111, and South Staffordshire Water.
But the true numbers of ransomware attacks in the UK each year are far higher, as organisations often do not report the compromises. This is substantiated by our own research, showing that of 294 attacker-reported attacks since 2020, 85% of ransomware incidents claimed by attackers go completely unreported by the victims or the media.
As the Ransomware threat landscape continues to evolve, with increasingly sophisticated Ransomware as a Service (RaaS) models and capabilities-for-hire, it is vital that UK organisations continue to be open and honest following attacks, so that others can learn from the attacks and help to build a more resilient UK.
Helpful links below:
- JUMPSEC’s Ransomware Report: https://www.jumpsec.com/uk-ransomware-trends-2022/
3. Tackling the Cybersecurity Skills Shortage
Arguably the biggest challenge facing the cyber security industry today is the shortage of skilled professionals. The worldwide skills gap is much reported and debated, with many organisations feeling the strain of not enough viable candidates to fill their vacant positions in an area that is seeing significant expansion in many organisations who are rightly beginning to take cyber security seriously.
The NCSC report notes that in the UK the cybersecurity industry employs nearly 53,000 people across 1,800 businesses, and is worth approximately £10 billion to the economy. In February, analysis revealed record levels of growth were apparent in the UK’s cyber security sector with a 24% and 13% increase in new businesses and jobs respectively. However, despite its size and significance to national security, over half of businesses lack basic technical cyber skills, and there’s still an annual shortfall of over 14,000 people in the UK cybersecurity workforce.
Like NCSC, JUMPSEC recognises the need to up our numbers by encouraging a broader spectrum of talent to join the cyber security industry, however, we must also acknowledge that retaining these skilled professionals is potentially an even greater challenge. Our recent Building Sustainable Services article details how work-related stress, burnout and disillusionment have been shown to be core issues for those opting to leave the industry (with 1 in 3 current cyber security professionals currently planning to change professions altogether). This is particularly true in the highly attritional field of defensive security which requires consultants to be on high-alert for excessively long working periods.
If we want to see the current investment being made in the next generation become truly effective, we need to ensure that the cyber security industry is ready to keep consultants engaged and passionate about their work – not just ensuring there is a pipeline of graduates ready to replace them. This is a core part of JUMPSEC’s philosophy, and one we consider vital to the future health of the cyber security industry.
Helpful links below:
- Building Sustainable Services article: https://www.jumpsec.com/guides/building-sustainable-services/
4. The Rise of MFA Bypass Attacks
According to the NCSC report there has been a significant increase in the amount of Multi-Factor Authentication (MFA) bypass attacks relying on Push Exhaustion. Push Exhaustion attacks are a tactic used by attackers to trigger a deluge of MFA acceptance prompts on a user’s phone, with the intention of forcing the user to eventually click ‘Allow’ to stop the flood of requests.
We regularly speak with organisations who have fallen into a false sense of security when it comes to MFA. While it may raise the cost to the attacker, it isn’t a 100% effective solution. Thankfully there a number of measures that can be implemented to combat MFA attacks:
- Disable MFA Push notifications, or if that is not possible enable number matching to increase security.
- Limit the number of push requests on their users’ devices, or quarantine when a certain number of requests are received in a given timeframe.
- Get affected users to change passwords for their account if possible to prevent hackers from continuing to log in and generate further MFA push notifications.
From a technical perspective, attackers have also demonstrated the ability to steal active session tokens – bypassing the authentication process. However, whilst human focused attacks succeed, attackers will continue to prefer less complex and technically challenging solutions to the problem.
Helpful links below:
- JUMPSEC’s Ransomware Report: https://www.jumpsec.com/uk-ransomware-trends-2022/
5. The Risk Posed by Emerging Vulnerabilities
The impact of emerging vulnerabilities such as the Log4shell exploit was noted as a key risk in the NCSC report – as the logging utility widely used Log4J remains a significant risk due to vulnerable instances remaining unpatched. The vulnerability demonstrates the challenge and risk posed by insecure underlying software libraries in users’ applications, and how quickly vulnerabilities can be weaponised by attackers at-scale to capitalise on such pervasive issues.
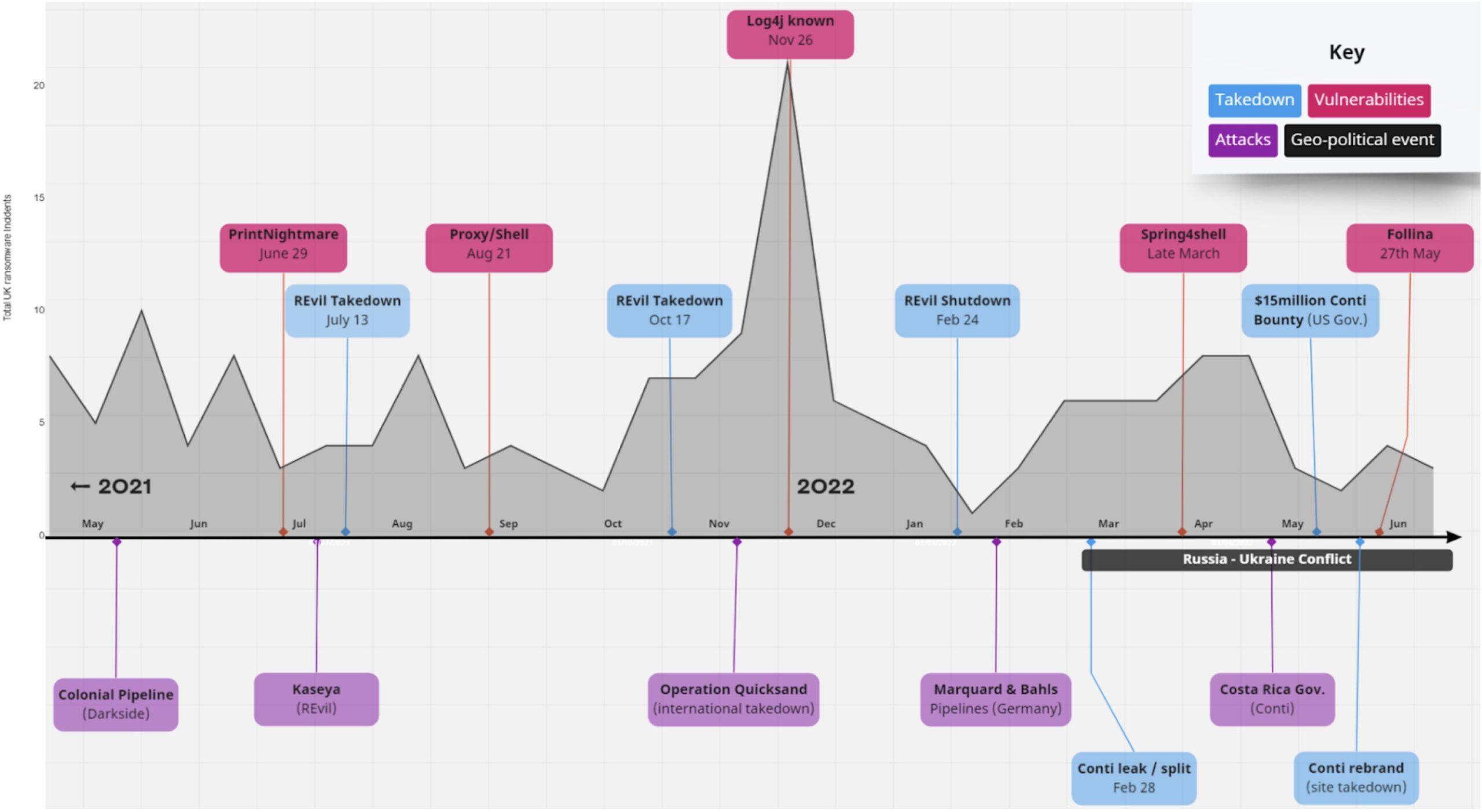
JUMPSEC’s recent Ransomware Trends report plotted the emergence of critical and widespread vulnerabilities against the total number of attacker reported ransomware attacks over a 12 month period. Our research indicates a clear correlation between the emergence of such vulnerabilities and periods of increased attacker activity, confirming the attacker’s readiness to mobilise and exploit issues as they arise.
This illustrates clearly that organisations must be fully aware of emerging vulnerabilities, ensuring they are mitigated and patched as soon as possible. Visibility of the ever-changing enterprise attack surface is vital to identifying both signs of current vulnerability, and inherently abusable or frequently vulnerable components that may become exploitable in the future.
Helpful links below:
- JUMPSEC’s Ransomware Report: https://www.jumpsec.com/uk-ransomware-trends-2022/
